Today I wanted to sftp into the webroot for my server (/var/www) but because of the way the permissions are set up the default ec2-user doesn’t have permission to do this. That directory tree is owned by the user “fred”, which otherwise doesn’t get used. I decided to allow ssh & sftp access to enable this.
There’s a pretty good guide to this in the AWS Documentation, but here’s exactly what I typed to get this to work. Note that I’m comfortable giving this information because my server is heavily firewalled, only allows connections from my IP, and requires a private key to log in.
Creating Amazon Linux User
First we create the user and give them a password. I’d already created the user a while back, but this is how it’s done. I’m not sure if you really need to give the user a password since login is by certificate only.
sudo su sudo useradd fred passwd fred
Amazon Linux Creating Keys
Next we generate the public and private keys, as the user tim, and copy them to the right place on the file system. We have to set very specific file and folder permissions for this to work. It’s good practice to set a password on the private key when prompted.
su fred ssh-keygen -f rsa mkdir .ssh touch .ssh/authorized_keys chmod go-w ~/ chmod 700 ~/.ssh chmod 600 ~/.ssh/authorized_keys cat fred.pub >> /home/fred/.ssh/authorized_keys
Amazon Linux Allowing User SSH & SFTP
Now we edit the sshd config to allow only ec2-user and tim to login
vi /etc/ssh/sshd_config PasswordAuthentication no AllowUsers ec2-user fred
Logging into Amazon Linux using Putty and FileZilla
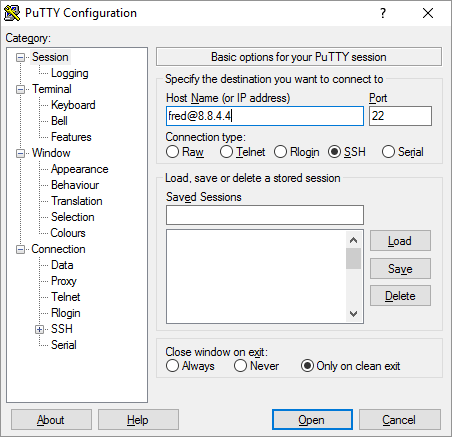
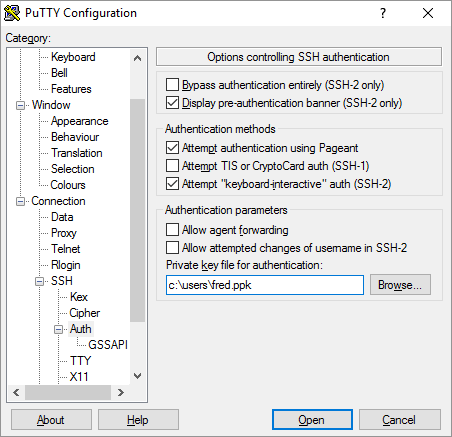
Next you have to download the private key to your PC and convert it to a ppk file using puttygen. You can read about this here. You test the login using putty with a host in the format below, and the private key in ppk format set under connection -> ssh -> auth
fred@ipaddress
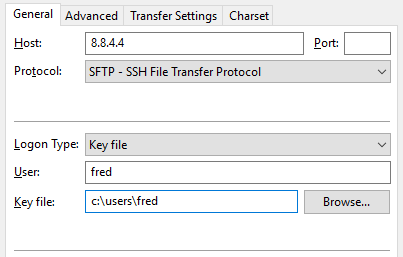
I use FileZilla as my FTP client. I set it up as per the screenshot below – IP address, “SFTP – SSH File Transfer Protocol”, with user and key set.